Website Security Strategies for Success
Today’s businesses face a number of potential online fraud and security risks. If you’re wondering what kind of security breaches and risks exist, you only need to watch the headlines to find the latest large corporation that has experienced a data security breach. Some common security risks include:
-
- Breaching of Confidential Information
- Stolen Passwords
- Corruption of Website Content
- Viruses that Spam and Hold Computer Contents Hostage
- Credit Card Harvesting
We’ll outline these security risks for you below and detail what your business can do to stay safe.
Stolen Passwords
Passwords are the key to everything important on the web. While best security practices dictate that passwords should be complex and vary for each log-in, this practice is often overlooked. That means if hackers steal passwords for administrative access to websites, the password can be used for other possible log-ins that access much more than just website content or email lists. With websites being stored on browser history, a stolen password is just the beginning of many potential problems.
Viruses that Spam and Hold Computer Contents Hostage
E-mail viruses are a common security risk for individuals as well as businesses. Once a digital intruder has a hold of your computer contents (potentially through a virus from an e-mail), your computer and e-mail contents are at their beck and call. This can range from spamming your email address book to further infect other contacts, stealing passwords, or even holding certain digital contents hostage until a ransom is paid.
Breaching of Confidential Information
Many businesses rely on credit card payments, taken either in the store, electronically or via multiple methods. Payment processing requires the collection of highly confidential information, which includes personal contact information (name, address, phone) and credit card information. Having access to such information would be a prime target for malicious activity and experiencing security leaks or breaches would be a public relations nightmare. However, breaches and leaks can be prevented when PCI security protocols are proactively implemented.
Corruption of Website Content
It may seem that having access to publicly available information is not a big deal, but that’s not what malicious hacker activity is after. Hackers and viruses can gain access to website content from the back-end, which can lead to website content corruption. Having a corrupt website can lead to loss of customers and credibility of your business.
Credit Card Harvesting
Since many company websites include forms for submitting credit card information, hackers and harvesters may target your website even if you’re not selling items they want. Here’s how credit card harvesting works – hackers or their bots run multiple (sometimes hundreds of) credit cards through your system to see which ones work. When a completed order is received, they know that they can use this credit card to make purchases on other websites or in stores (if they have the physical cards).
To limit this practice, businesses should consider requiring CAPTCHA and address verification (AVS) on your secure website forms. AVS is one of the most widely used fraud prevention tools for online transactions. AVS checks compare the billing address used in the online transaction with the issuing bank’s address information for the cardholder. If a hacker has a list of stolen credit cards, he likely doesn’t have this information as well.
How do businesses avoid these security risks?
All of these risks are frightening to experience and detrimental to the reputation of your business. What can be done? Here are some steps that can be taken to assure that your organization is protected and utilizes best practices in website security.
Install SSL Certificates & Use Only HTTPS Websites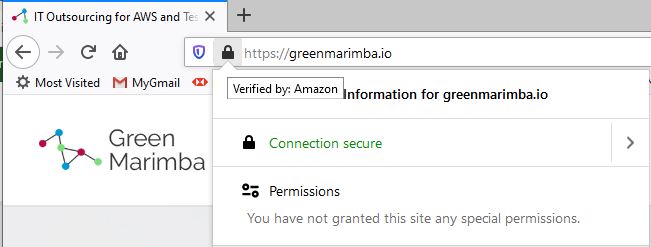
An SSL (secure sockets layer) certificate ensures a secure connection is established between a website user and the server where the website data originates. It is signified in a website’s URL by the use of HTTPS (instead of just HTTP). Secure sessions use encryption methods to ensure that data can be more safely transferred and more difficult for hackers to intercept. This is one of the easiest and most important tactics in your website security toolkit.
Ensure Software Is Hosted Securely & Automatically Updated
Website hosts should implement updates on a regular basis. This is important because outdated code that does not constantly patch-in bugs can leave room for hackers to breach information through the website. Good website hosts understand that fixes need to be applied on a regular basis as new bugs are discovered, so maintaining regularly automated updates is part of the preventative measures of security risks.
Contact us for secure, cloud hosting options.
Install Antivirus Software
Antivirus software checks for such malicious activity within your computer and takes proactive steps to block viruses from infecting your computer. The software also allows for regularly screening your computer so that your computer continues to be virus-free.
Backup Servers and Data
Website contents and data should regularly be backed up in the case of data loss. For example, if your computer contents are held ransom because of a virus, the only way to get rid of it is to wipe the entire computer clean. That means if your data isn’t backed up, it can potentially be permanently lost. Data can be wiped clean in some security breach incidents, as well, and instead of starting over because the contents and data were stored only in one place, having a back-up can save time, money and resources. Moving your website data to a secure cloud environment makes backups and restores easy.
Establish PCI Compliance for Credit Card Processing
Credit card processing comes with its own set of compliance guidelines and standards. All organizations that accept credit cards must abide by Payment Card Industry (PCI) standards. When choosing a credit card processor for your donations, be sure to ask about how they comply. Some guidelines should include encryption of transmitted data and maintaining that all network connections are secure during the transmission. Request their security information policy so that it is clear that the processor is truly compliant.
Be Sure to Use Secure Passwords
While it’s tempting to lazily use “password123” as your password, hackers often crack passwords because of how easy they are to guess. A secure password includes a combination of lowercase letters, upper case letters, numbers and special characters (if the password requirements permit). Once you have a password, also be mindful not to share it with others or even other websites. Follow the rule that you should share your passwords as you would share your toothbrush.
To automatically store and manage passwords, try using a secure password tool such as RoboForm.
Utilize E-mail Safety Precautions
Of course, business safety precautions don’t just stop at your website. After all, many of your staff members are probably communicating daily via email. These are some steps to take to avoid getting a virus through emails:
- Don’t even open emails that look suspicious
- Don’t click on links or downloads that are not verified or look like suspicious URLs
- If you receive a spam email, notify the owner of the email that their email has been hacked so that they can change their password
- If you have personally had your email hacked, immediately change your password and notify your IT department of the incident
Conclusions on Website Security for Businesses
Following these guidelines on how to maximize your website and data security, taking the steps to become more secure will come seamlessly. Green Marimba offers free PCI resources and data security protection, as well as WordPress managed hosting services.
